Attackers use Cloudflare Tunnel to proxy into victim networks
4.6 (177) · € 28.99 · Auf Lager

Hackers Abuse Cloudflare Tunnels to Gain Stealthy Access
What is DNS tunneling, and how can it be prevented? - Quora
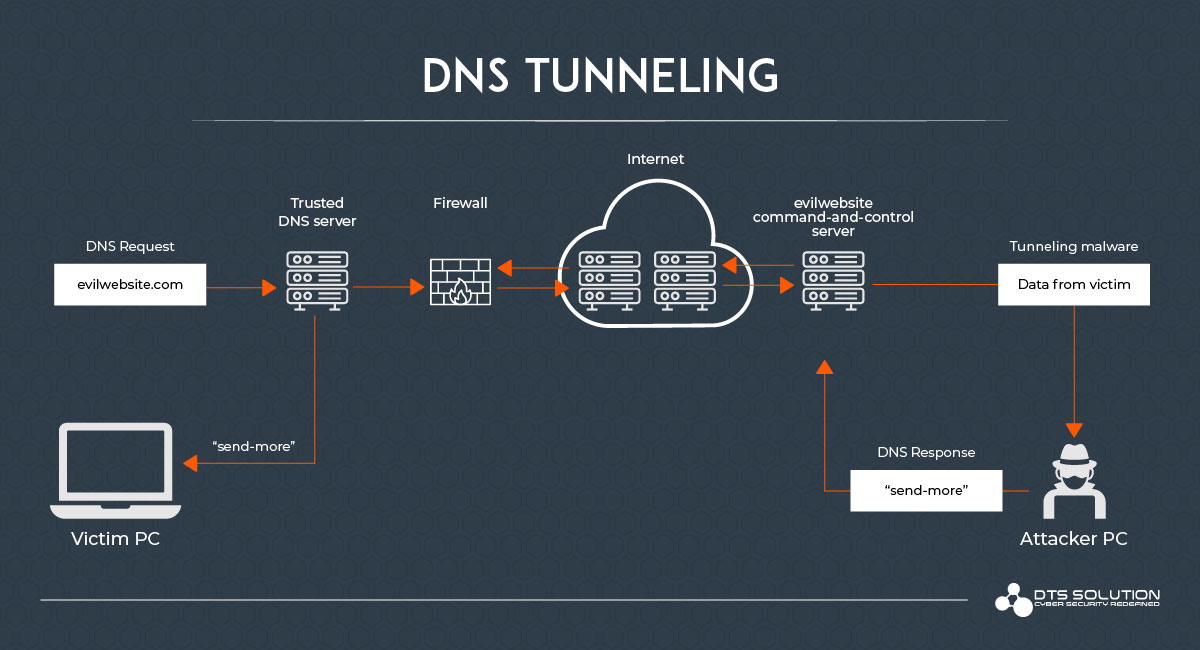
DNS Tunneling and Countermeasures in an Enterprise

Tunneling Attacks
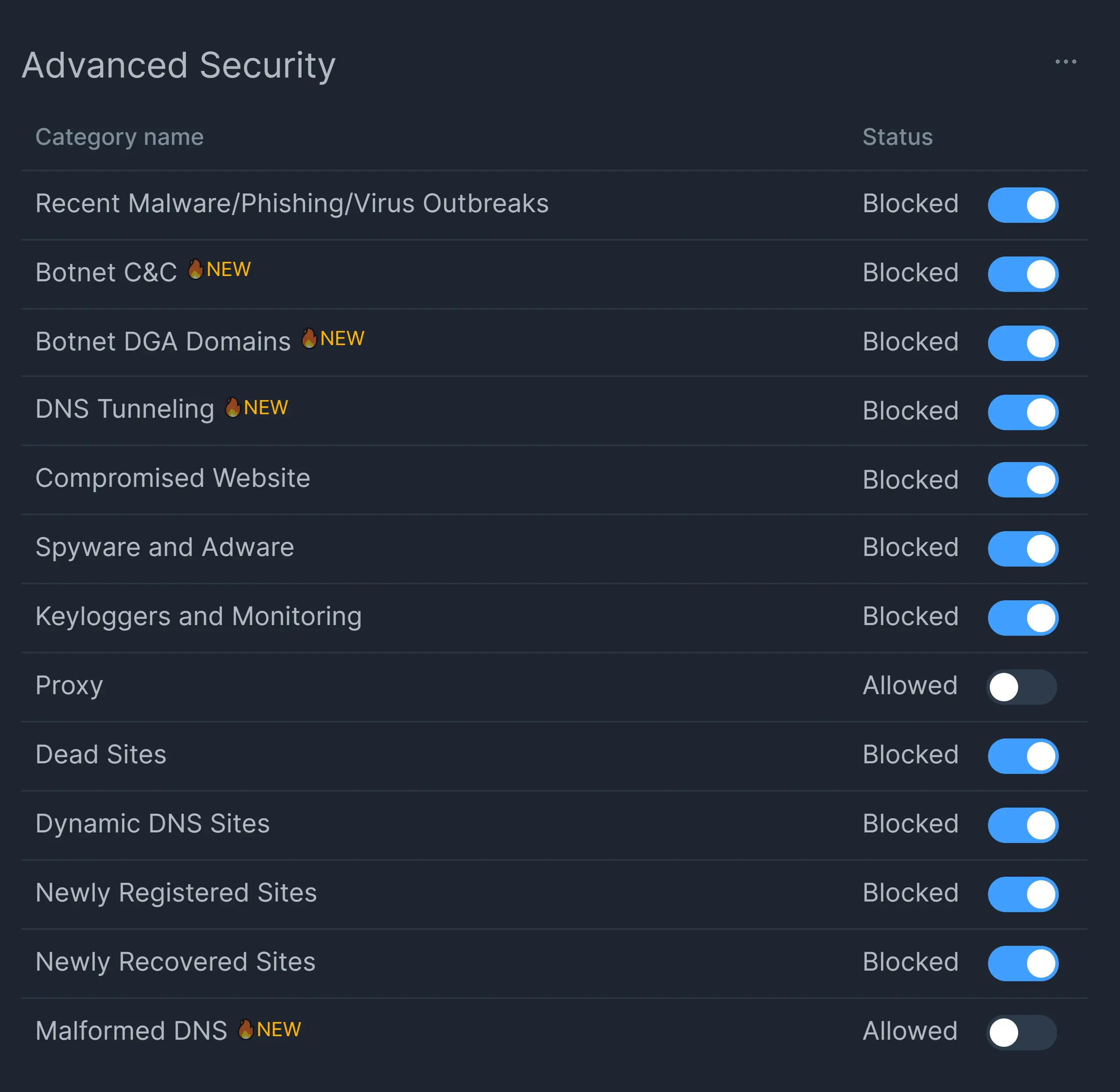
What is DNS Tunneling? Detecting, preventing DNS Tunneling Attacks

Man-in-the-Middle Attack Detection and Prevention Best Practices
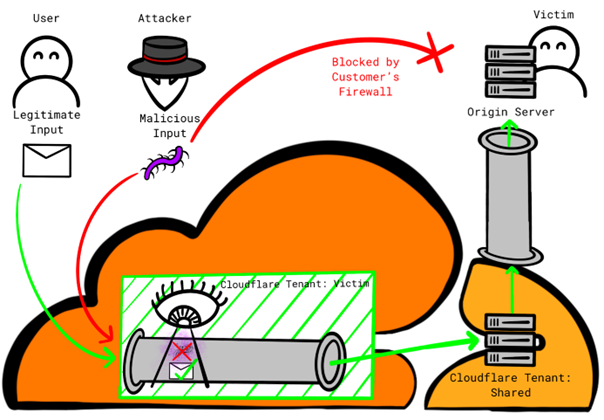
Using Cloudflare to bypass Cloudflare – Certitude Blog
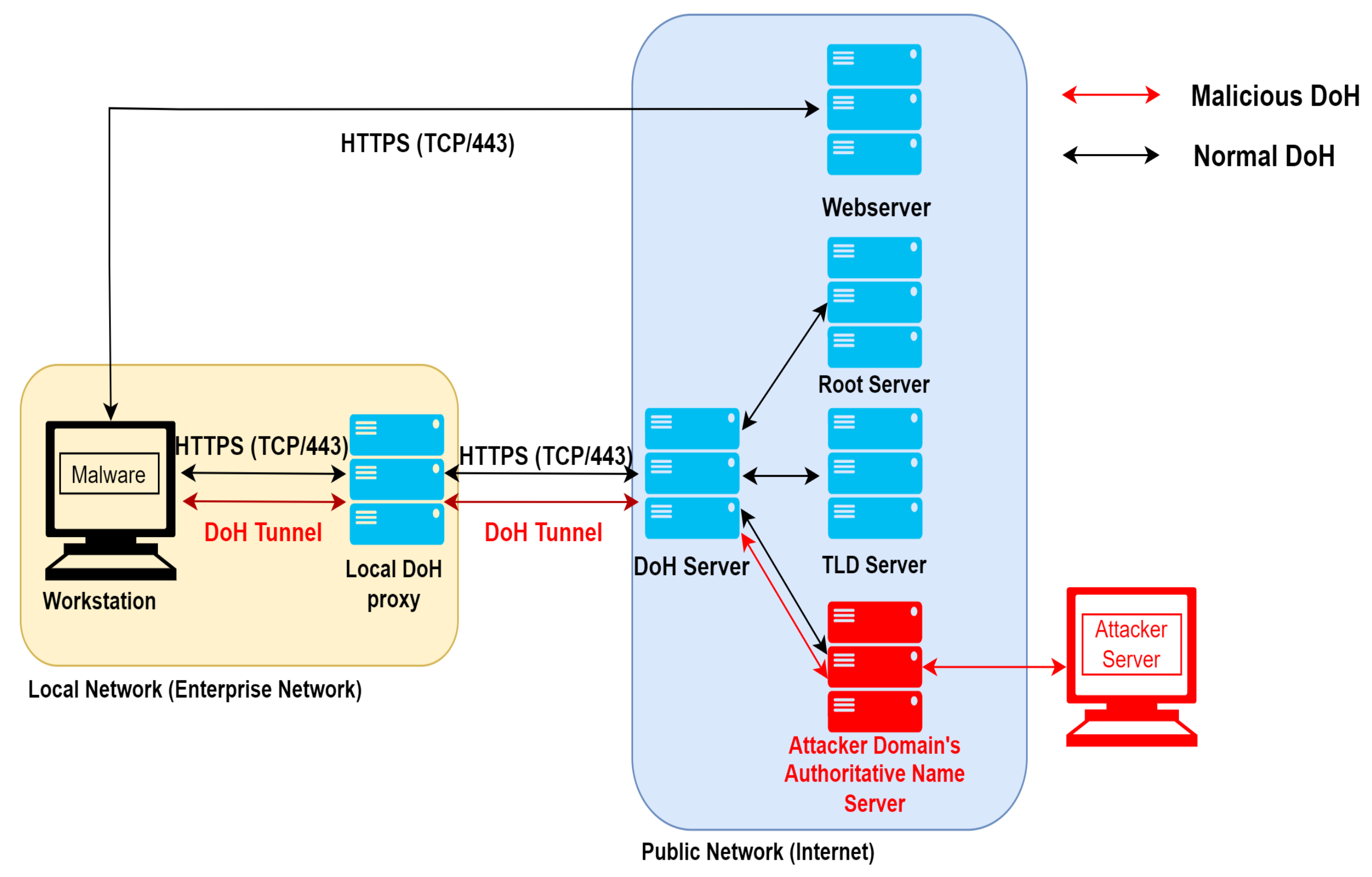
Applied Sciences, Free Full-Text
New Zardoor backdoor used in long-term cyber espionage operation targeting an Islamic organization

Toward the mutual routing security in wide area networks: A scoping review of current threats and countermeasures - ScienceDirect

The F5 DDoS Protection Reference Architecture (Technical White Paper)

weewx server?

PDF) DoH Tunneling Detection System For Enterprise Network Using Deep Learning Technique
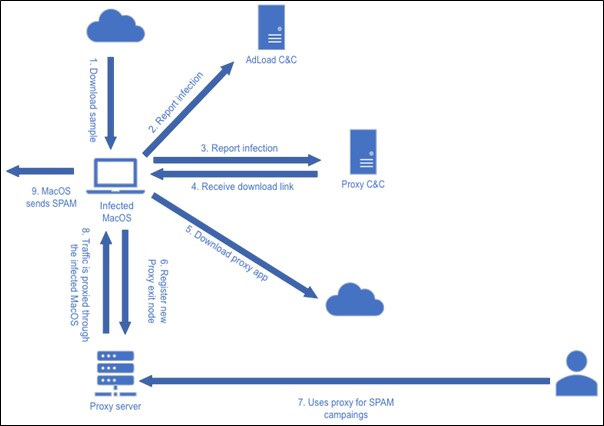
Risky Biz News: Russia blocks OpenVPN and WireGuard VPN protocols











